ME-TLS: Middlebox-Enhanced TLS for Internet-of-things Devices
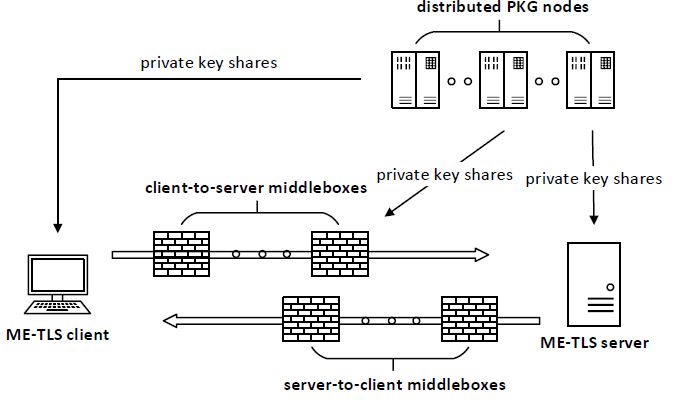 Fig.1 System architecture
Fig.1 System architecture
Abstract
In-network middleboxes are vital for Internet-of-things system security, but the widely adopted Transport Layer Security (TLS) protocol blinds application-level middleboxes due to the encryption of traffic data. To resolve this problem, many solutions have been proposed to date. Among them, SplitTLS is widely adopted in the industry by proxy manufacturers. It requires TLS client to install customized root certificates and incurs additional security flaws, e.g., disabling server authentication and using weak cipher suites. Another approach is to customize the TLS protocol where middleboxes are enabled via either performing handshake directly with TLS endpoints, or receiving session key materials in an out-of-band manner. Overall, current solutions would either jeopardize the original TLS handshake procedure, or incur additional overheads on the endpoints.
In this paper we design a new middlebox-enhanced TLS (ME-TLS), which enables endpoints to introduce authenticated middleboxes into a TLS session while control middleboxes’ access permission and processing order of traffic data. Particularly, in our proposed ME-TLS, the handshake structure of TLS keeps unchanged and middleboxes work in a passive manner. That is, middleboxes in the ME-TLS could recover session key materials by monitoring handshake messages passively instead of interacting with endpoints, secondary secure channels for key transmission are also not needed in our ME-TLS. We implement our ME-TLS based on TLS 1.3 protocol and evaluate its performances. The experiment results demonstrate that our proposal is practical and deployable for real-world IoT scenarios.