Security of Auditing Protocols Against Subversion Attacks
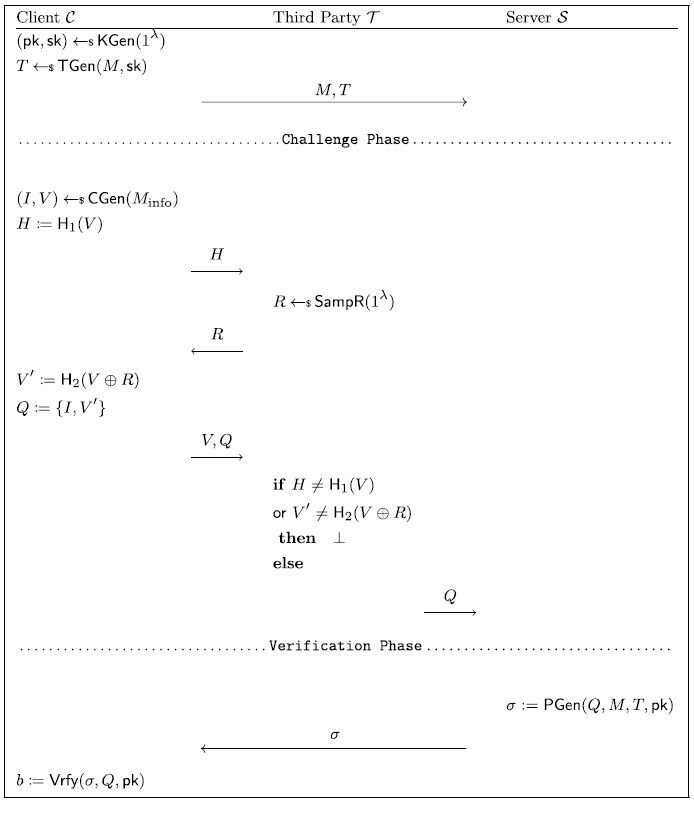 Fig.5 A general AS-SA resilient auditing protocol with index-coefficient challenge
Fig.5 A general AS-SA resilient auditing protocol with index-coefficient challenge
Abstract
In 2013, the revelation of Edward Snowden rekindled cryptographic researchers' interest in subversion attacks. Since then, many works have been carried out to explore the power of subversion attacks and feasible effiective countermeasures as well. In this work, we investigate the study of subversion attacks against cloud auditing protocol, which has been well-known as useful primitive for secure cloud storage. We demonstrate that subverted auditing protocol enables the cloud server to recover secret information stored on the data owner side. Particularly, we first define an asymmetric subversion attack model for auditing protocol. This model serves as the principle for analyzing the undetectability and key recovery of subversion attacks against auditing protocols. We then show a general framework of asymmetric subversion attacks against auditing protocols with index-coefficient challenge. To illustrate the feasibility of our paradigm, several concrete auditing protocols are provided. As a feasible countermeasure, we propose a subversion-resilient auditing protocol with index-coefficient challenge.