Asymmetric Subversion Attacks on Signature and Identification Schemes
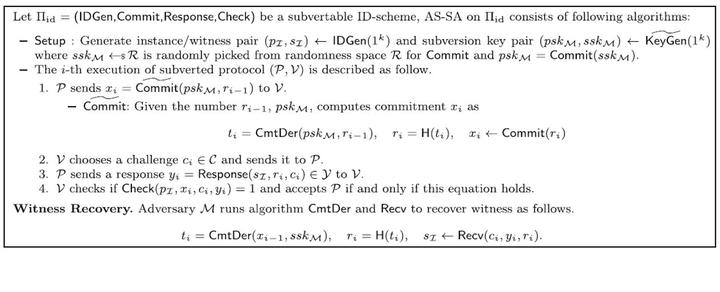 Fig.8 A universal AS-SA on subvertable ID-scheme
Fig.8 A universal AS-SA on subvertable ID-scheme
Abstract
Studies of subversion attack against cryptosystem could be dated to several decades ago, while the Snowden revelation in 2013 has set off a new wave of exploring possible approaches to protect or subvert cryptography primitives in practice. Inspired by kleptographic attacks proposed by Young et al. [Crypto’96], we present the asymmetric subversion attack on signature and identification schemes in this work. Our contributions is summarized as follows:
- We present the asymmetric subversion model for signature and identification schemes. The properties of our model are stronger than that of existing subversion model proposed by Giuseppe et al. [CCS’15] and show higher requirement in attack goal.
- We propose the notion of splittable signature scheme and give a universal asymmetric subversion attack on such schemes. Our attack is independent of secret key size and more efficient than symmetric attacks introduced by Giuseppe et al. [CCS’15].
- We introduce the asymmetric subversion attack on a special type of identification schemes and show that it can be transformed from splittable signature scheme.
Type
Publication
Personal and Ubiquitous Computing