Identity-based revocation system: Enhanced security model and scalable bounded IBRS construction with short parameters
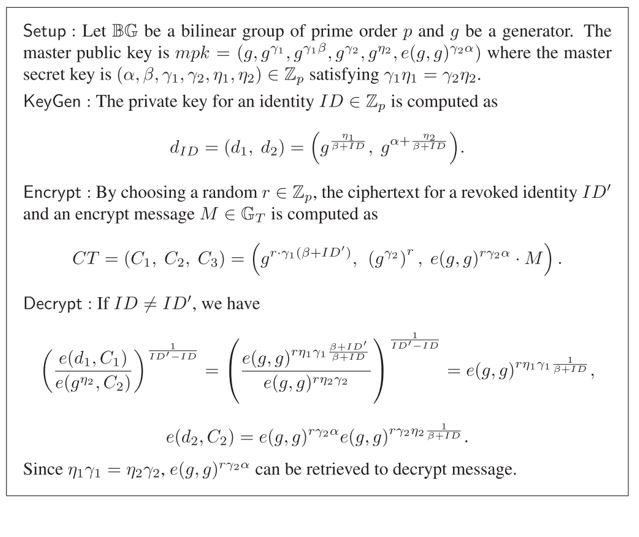 Fig.1 Our basic IBRS scheme for one single revoked identity
Fig.1 Our basic IBRS scheme for one single revoked identity
Abstract
Identity-based revocation system (IBRS) produces a ciphertext based on the revoked identities such that this ciphertext can only be decrypted by the private keys of non-revoked identities. IBRS can be classified into unbounded IBRS and bounded IBRS, depending on whether to set a maximal revocation number (e.g., N) or not. Compared to unbounded IBRS, existing bounded IBRS schemes have the advantage of short ciphertexts, however, they cannot support an increase of N and have to fix a large N to provide the revocation. This compromises the computational efficiency, which is linear in N. To bridge this gap, we are interested in exploring whether N can be dynamic. Precisely, N is initially set as a small number and increased into a larger one when more than N identities are revoked, while this increase does not affect other non-revoked users in the system. In this paper, motivated by the security of bounded IBRS with a dynamic N, we define an enhanced security model, which allows the corruption of any polynomial number (e.g., n) of private keys, independent of N. It augments existing security models by running different challenges when n ≤ N and n > N, respectively. The enhanced security model suits both unbounded IBRS and bounded IBRS with a general description that can be “empty” for unbounded IBRS or a special N for bounded IBRS. Then, we propose a scalable bounded IBRS scheme and are able to prove its security in an enhanced security model. The increase of N incurs no changing on all of the existing private keys and the only cost is a slight expansion of the master public keys. Our proposed scheme also has short ciphertexts and private keys, comparable to the state-of-the-art (bounded) IBRS schemes.