Practical Privacy-Preserving Deep Packet Inspection Outsourcing
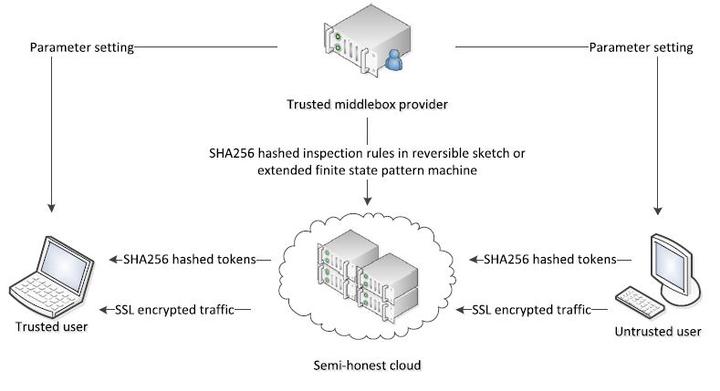 Fig.2 System architecture
Fig.2 System architecture
Abstract
Hardware-based middleboxes are ubiquitous in computer networks, which usually incur high deployment and management expenses. A recently arising trend aims to address those problems by outsourcing the functions of traditional hardware-based middleboxes to high volume servers in a cloud. This technology is promising but still faces a few challenges from different aspects, including privacy concerns, middlebox functionality, and performance. In this paper, we propose two practical approaches to implementing a cloud-based DPI middlebox. The outsourced DPI middlebox performs payload inspection over encrypted traffic while preserving the privacy of both communication data and inspection rules. Our first approach employs amodified reversible sketch structure,which is used for efficient error-free membership testing, and our second approach extends the famous AC pattern matching algorithm to the cipher text domain.We utilize unkeyed one-way hash functions instead of complex cryptographic protocols to achieve the privacy preservation requirements. Our system supports a wide range of real-world inspection rules.We conduct evaluations on the ClamAV rule set, and the experiment results demonstrate the effectiveness of our proposals.