Privacy-Preserving Data Search and Sharing Protocol for Social Networks through Wireless Applications
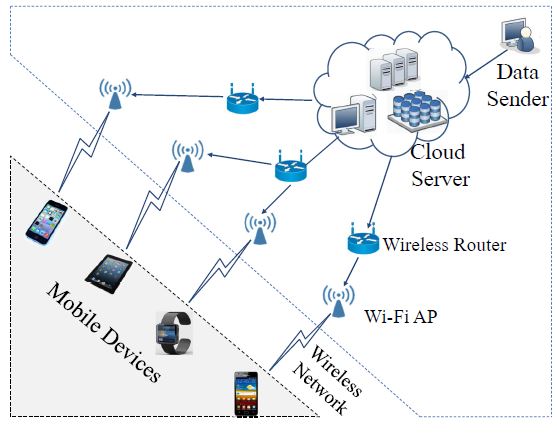 Fig.1 Encrypted data shared in cloud
Fig.1 Encrypted data shared in cloud
Abstract
Data search and sharing are two important functionalities in social networks. The social network users can form a peer-to-peer group and securely and flexibly search and share cloud data through wireless applications. When the number of users increases, the communication, storage, and computational overheads will be increased, and the quality of services such as searching and data sharing for clients could be affected. In order to solve these problems, we formalize an ID-based multi-user searchable encryption (IDB-MUSE) and formally define its security model, where the security notions accommodate indistinguishability against insider’s keyword guessing attack, indistinguishability against chosen keyword attack, and indistinguishability against insider’s identity guessing attack.We present an IDB-MUSE scheme, where the index and search trapdoor are of constant size.We formally prove its security properties. To improve the search efficiency, we divide the computation of the trapdoor into two phases, that is, the offline phase and the online phase. The computation cost for the online phase trapdoor remains constant with respect to the number of users. Based on the IDB-MUSE scheme, a privacy-preserving data search and sharing protocol is proposed, where only the authorized user can access the shared group data. It captures the properties of source authenticity, data and search pattern privacy-preserving, anonymity, and request unlinkability. The experimental results show that the protocol is practical for wireless applications. Copyright © 2016 John Wiley & Sons, Ltd.